Remote connectivity is about to have its heyday.
Thanks to the Internet of Things, remote connectivity is no longer just for enterprise IT applications. The ability for companies to remotely connect to their products…large or small, enterprise or consumer…is about to explode. It opens the door to providing proactive service, gathering data, reducing costs, and much more.
But with this expansion comes the need to rethink the technology
The go-to way to remotely connect to products and customers has been through VPN, but that’s not going to fly as companies enable broader and broader reach. Rather, we need robust capabilities in a lightweight, secure, and simple platform.
Providers in telecom, health, hospitality, finance, automotive, aerospace, retail, and more all stand to either hop on this change or see it sink their ship.
Personally, I’m beyond excited for this revolution. I’ve spent over a decade working in connectivity. I’ve managed global teams responsible for setting up and maintaining connections. I’ve led corporate connectivity strategy. I’ve been through modems, VPNs, and purpose-built solutions….even for the Department of Defense.
But you may have some anxiety. If your company is entering this space or you’re looking to mature, there is so much to consider. How should you choose the right remote connectivity solution?
What Remote Connectivity and Monitoring Enables
Remote connectivity gives you the ability to stay synced with your products and customers like never before. It allows game-changing levels of service.
“National Instruments Executive Vice President Eric Starkloff stated companies are most interested in instrumenting their operations, ‘looking for events that are a warning of impending failure’ in systems or squeezing additional efficiency out of their operations.” (ArsTechnica)
At a high level, remotely connecting to your products enables you to:
- Service remotely, preventing dispatches and returns.
- Proactively service with automation, prolonging the product life and improving customer satisfaction.
- Receive diagnostics, alarms, and warnings.
- Collect real first-hand data about your products and customers.
- Integrate with 3rd parties.
These apply whether you sell construction vehicles, airplanes, or wearable health devices.
“Smart connected products offer exponentially expanding opportunities for new functionality, far greater reliability, much higher product utilization, and capabilities that cut across and transcend traditional product boundaries. The changing nature of products is also disrupting value chains, forcing companies to rethink and retool nearly everything they do internally.” (How Smart, Connected Products are Transforming Competition by Harvard Business Review).
Further factors to consider include:
- Security
- Performance
- Simple client-side administration
- Firewall-friendly configuration
- File transfer capabilities
- Resource usage
- Proactive capabilities
Security and Privacy Really, Really Matter
Security has always been a big deal in the enterprise connectivity space. I have been in charge of projects to set up remote connections into the hearts of big companies. We were setting up an “in” right to the data centers of Fortune 500 companies. Were they worried about security? You better believe it.
Does security and privacy matter any less if you are looking to create a connected vehicle or watch? Not by a long shot.
In fact, Harvard Business Review says “underestimating security and privacy risks” is one of the top 5 mistakes to avoid (How Smart, Connected Products are Transforming Competition).
You don’t want your products to be responsible for leaking data of your customers, whether individuals or companies.
A couple of the key considerations:
1. Outbound-only communication is highly secure
Your solution shouldn’t require inbound ports to be opened. Your devices should only reach out to known destinations.
2. Your device must allow updates
New vulnerabilities pop up constantly. You must have the ability to remotely deliver firmware and software updates, otherwise your solution will become increasingly risky over time.
“New threats will emerge through 2021 as hackers find new ways to attack IoT devices and protocols, so long-lived “things” may need updatable hardware and software to adapt during their life span.” Gartner
Bazooka or Sniper Rifle? Should I use a VPN?
VPNs are the go-to solutions for setting up connections in the B2B world. But are they the right way to handle connections out to your devices?
VPNs offer a robust set of features and allow you to do extensive provisioning and configuration. However, with this flexibility comes complexity and overhead. This complexity exists both on your end and the customer’s end, which means ongoing coordination…not scalable.
After being deep in the trenches on setting up and maintaining B2B VPNs for products, I can assure you this solution is often overkill. And complicated to maintain. You’d like to think a change management admin remembers every vendor’s unique requirements…
Bottom line–when you’re trying to hit something very specific, bazookas are rarely the answer. Go for something more purpose built.
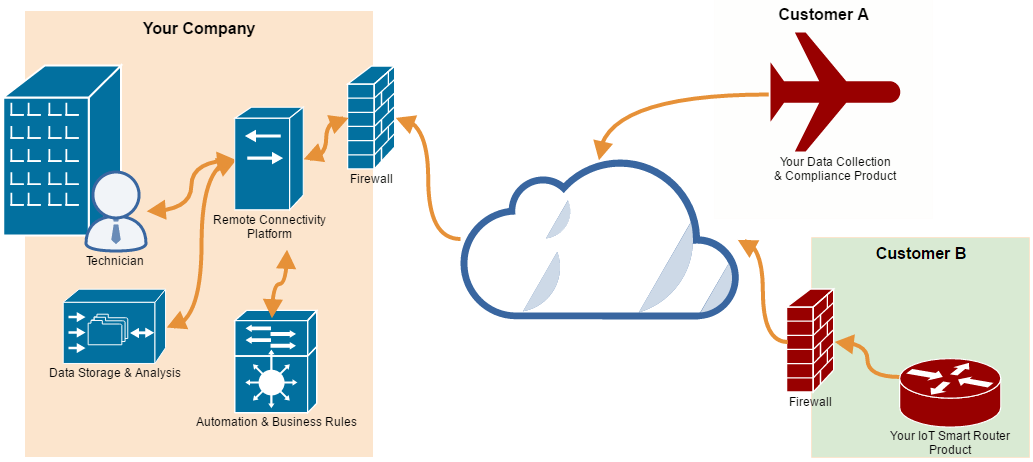
The sniper rifle: purpose-built Remote Connectivity model
In order to meet the needs of security and simplicity, lightweight architecture that operates in a simple outbound manner is often the best for connecting field devices.
The connections go out using HTTPS outbound over port 443, using standard secure access over the internet. If your devices use a customer’s internet connection, you’ll be able to piggyback on existing rules with no firewall changes required. If your product will have its own internet connection, such as cellular, you’re set too.
Security is inherent in this solution. Since it is outbound only, the device can be hardened to block inbound requests.
Further, when it connects out, it is going to a known destination and expects a known answer. This is much more difficult to spoof or get in the middle of.
Additionally, devices connecting in this model can self-register. If you have a unique identifier schema (serial number), devices can link back to you and register themselves. So no more coordinating with field installs to register connectivity and devices.
What about inbound connections and servicing?
The beauty of these light-weight outbound connections is they can still establish a tunnel. Through this outbound connection, if the response on the far end checks out, the device can allow communication to tunnel back to it.
Through this HTTPS outbound channel, technicians and automated tools can communicate back using the protocols needed, such as:
- HTTPS
- SSH
- SFTP
- RDP
- More
Incredibly flexible.
Pulse of life
By going with an outbound-only model, the device itself must reach out to the service center on regular intervals. This can be done with short or long polling. But regardless of the method, an “I’m alive” signal needs to happen. This is how the device sends info and checks for remote connection requests.
The advantage of this is you can be aware of connectivity problems before the product has a problem. Generally with VPNs, you uncover a connection problem at the same time you go to service a product. Not good.
The Technology Stack of Purpose-Built Connectivity
Alright, if this is making sense as the architecture to connect your things, you probably now have even more questions. In upcoming posts, I’ll dive into whether you should build or buy. And whether you should go with a hosted solution or not.
But perhaps you can answer those questions for yourself by having a peak under the hood. This is not a solution for very small electronics (such as wearables), but will work for many applications where a small device can be included or installed alongside existing software/firmware.
Conclusion
This post is just scratching the surface on providing remote connections and management to your products. But hopefully it gives you some good food for thought on the architecture, which really isn’t that complicated. For something to be scalable and lightweight, simple is definitely better.
Are you getting the most out of your products remotely? What have your trials and tribulations been? I’d love to hear in the comments below.
[embedit snippet=”after-article-getresponse”]